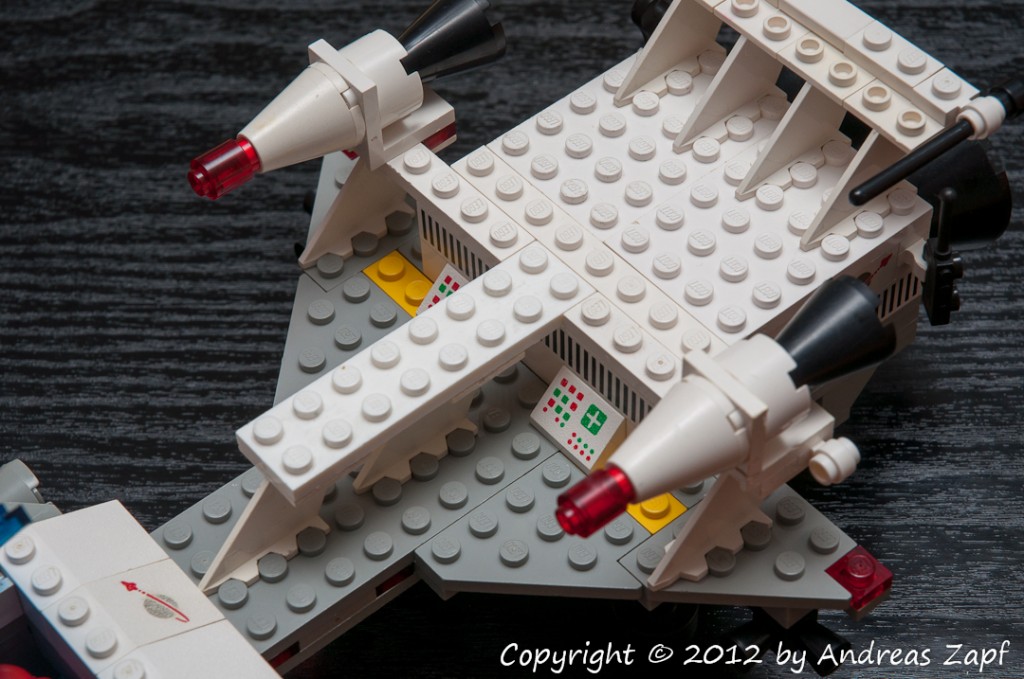
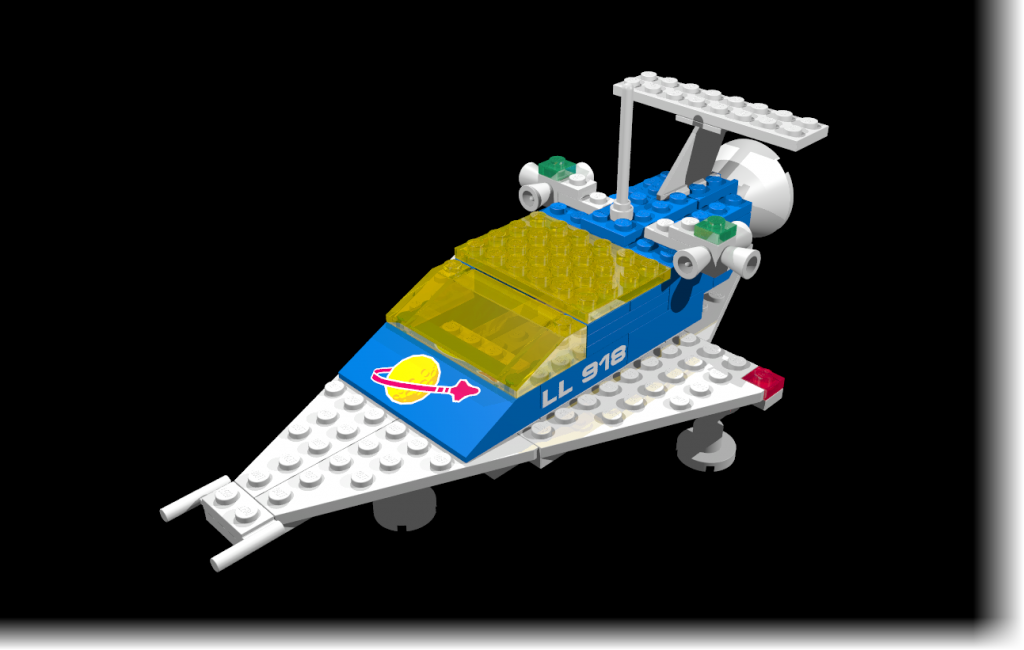
Here is another Classic Space set – this time from 1982. The LEGO Set 6950 – the Mobile Rocket Transport – comes in the all-so-familiar gray-yellow color scheme, complete with a detachable large Rocket.
 This one is a set I never owned before – so it is not in my original collection from the early 80’s but I did get it reasonably priced at eBay (again, I actually got two because the other one came in a set later).
This one is a set I never owned before – so it is not in my original collection from the early 80’s but I did get it reasonably priced at eBay (again, I actually got two because the other one came in a set later).
Like before, the set came “partially assembled” and the first step is taking it apart and running it through the dishwasher at a low-temperature program. I really like the method, it is working nice and clean.
 Unlike so many other sets that I own, this one comes with a specialty: the original box! Usually, when the box comes into play, prices soar at eBay but for one reason or the other, this did not happen for this particular auction.
Unlike so many other sets that I own, this one comes with a specialty: the original box! Usually, when the box comes into play, prices soar at eBay but for one reason or the other, this did not happen for this particular auction.
One of the advantages having the original box is that they usually held “alternate” model ideas – things you could also build from the set but which are not covered by any instructions officially provided by LEGO.
 This kind of proofs my point that I favor the Classic Space Theme over any of the new space themes such as “Star Wars” or “Alien”: being made from really generic bricks and not following any fixed motive (such as a Star Destroyer) they tend to really encourage creativity. You can build whatever you can imagine – as long as you got the bricks to support it.
This kind of proofs my point that I favor the Classic Space Theme over any of the new space themes such as “Star Wars” or “Alien”: being made from really generic bricks and not following any fixed motive (such as a Star Destroyer) they tend to really encourage creativity. You can build whatever you can imagine – as long as you got the bricks to support it.
To comment on the model itself: it is in really good condition – especially the transparent yellow parts are in really good shape, very little scratches and wear of time. And the only thing found missing is a flat black 2×2 disc.
Another thing about the model which I really like is its touch with LEGO Technic. Some other models use the bricks but this one really makes use of them by coming with a flexible all-terrain wheel suspension.
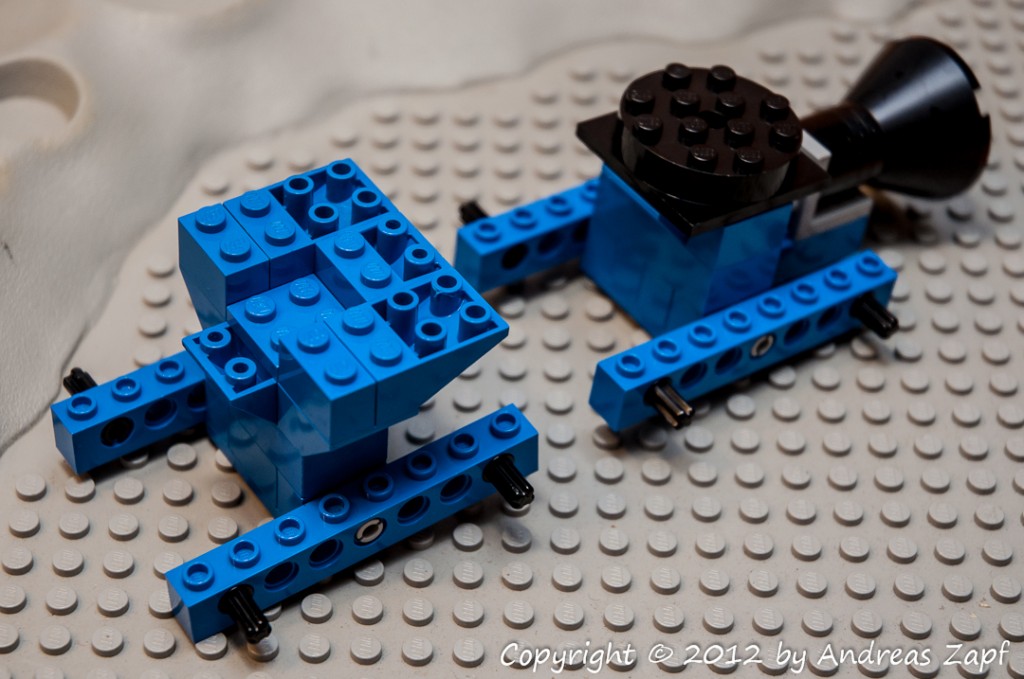 Above is a picture of the suspension section – front is left. As you can see, it will have eight large wheels mounted in pairs to four individually adjustable axles.In addition, the rear section in addition can be rotated to provide full maneuvering flexibility.
Above is a picture of the suspension section – front is left. As you can see, it will have eight large wheels mounted in pairs to four individually adjustable axles.In addition, the rear section in addition can be rotated to provide full maneuvering flexibility.
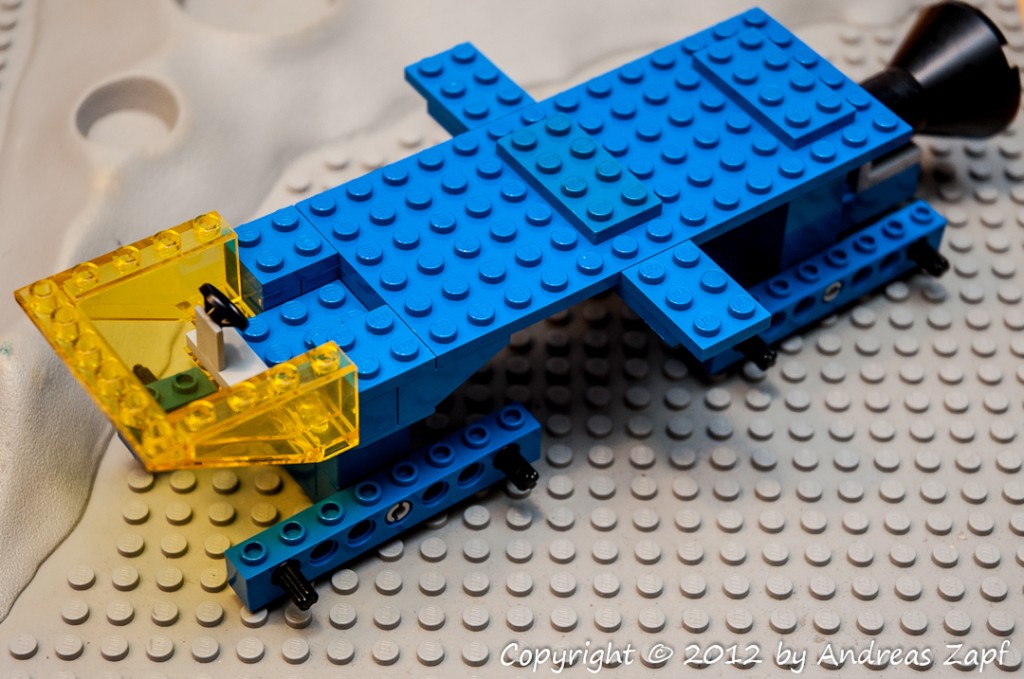 Both section are held in place by a large 6×14 plate which serves as the foundation of the platform itself. The front will also host the cockpit and (later) the control section.
Both section are held in place by a large 6×14 plate which serves as the foundation of the platform itself. The front will also host the cockpit and (later) the control section.
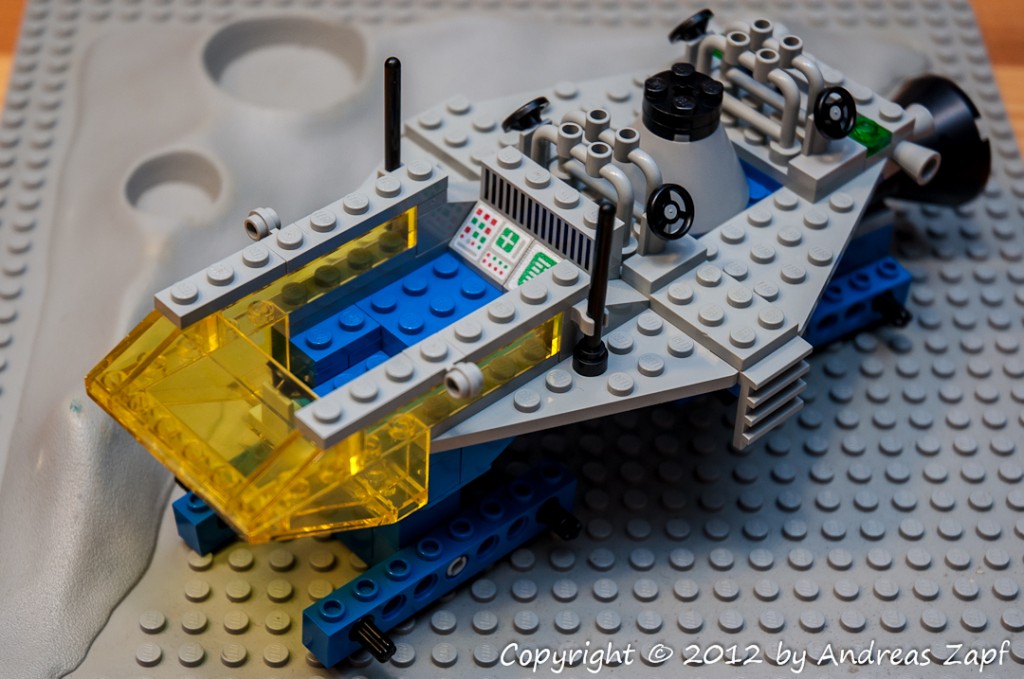 The platform itself is composed from four wing elements, access ladders, control thrusters and four steering wheels to control the crane, which will be mounted on the massive support structure seen above.
The platform itself is composed from four wing elements, access ladders, control thrusters and four steering wheels to control the crane, which will be mounted on the massive support structure seen above.
 With the wheels mounted and the lower hinge in place, the Rocket Transport is almost finished. Another hinge and a small platform mounted on top of it will hold the rocket in place.
With the wheels mounted and the lower hinge in place, the Rocket Transport is almost finished. Another hinge and a small platform mounted on top of it will hold the rocket in place.
The rocket itself is pretty complex – maybe the most complex one in the theme and serves the model just right.
 Fully assembled and placed on an original LEGO 306 Crater Plate, the dimensions and size of the model become apparent – here are some more close-up photos of the assembled model.
Fully assembled and placed on an original LEGO 306 Crater Plate, the dimensions and size of the model become apparent – here are some more close-up photos of the assembled model.
 The Cockpit section above – and the aft section below. Note the rocket’s clever setup with the side thrusters – very nice model design.
The Cockpit section above – and the aft section below. Note the rocket’s clever setup with the side thrusters – very nice model design.
 Finally, we can also see the hinges in action while the rocket is lifted into a launching position. The box stabilizing the rocket can be opened and the launch vehicle would simply drive forward to pull free.
Finally, we can also see the hinges in action while the rocket is lifted into a launching position. The box stabilizing the rocket can be opened and the launch vehicle would simply drive forward to pull free.
 The final images shows the wheel suspension in action – the front right gear easily adapting to the terrain of the crater plate while the front left section remains level on the base plate.
The final images shows the wheel suspension in action – the front right gear easily adapting to the terrain of the crater plate while the front left section remains level on the base plate.